12 Types of Computer Viruses and How to Protect Against Ransomware?

What is a computer virus?
A computer virus is a program created for the purpose of attacking a computer’s security system, causing disruption, manipulation, and destruction of data within the targeted computer. It is often used to inflict harm upon individuals, government entities, businesses, as well as to gain military and national security advantages, and for espionage involving critical data. An important characteristic is its ability to spread to other computers or electronic devices through online platforms like websites or social media, as well as storage devices such as flash drives or external hard drives. Due to this capability, computer viruses can cause significant damage if a computer lacks effective security measures, especially when not equipped with antivirus software capable of comprehensive protection against various forms of cyberattacks and crimes.
What are the types of computer viruses?
The operation of a computer virus involves infiltrating and embedding itself in the computer’s random access memory (RAM). Afterward, it gradually inflicts damage to the computer’s operating system, depending on the virus’s intended purpose. This can encompass data destruction, data theft, or disruption of normal computer functions. There are various types of computer viruses, typically categorized into seven types as follows:
1. Worm
One of the dangerous types of computer viruses that can cause severe damage due to its ability to rapidly spread to other computers and electronic devices. Additionally, it can highly disrupt the functionality of the computer. Moreover, due to its rapid spread, it becomes significantly challenging to eliminate, often requiring the use of a high-capacity antivirus to effectively counter the worm virus that invades and compromises the computer’s operating system.
2. Boot Virus
This type of computer virus is embedded within a Flash drive and immediately attacks the computer upon the Flash drive being accessed. When the hard disk starts reading the aforementioned Flash drive, the virus jumps to the Master Boot Record before moving to the memory unit and initiating its operation. When a computer infected with this virus is started, it may not exhibit clear symptoms, but it usually spreads to other Flash drives while the computer is shutting down. This method allows the virus to propagate to other computers without being detected.
3. Macro Virus
This is a type of computer virus commonly encountered during work, especially in office tasks related to various document programs. Macro viruses insert themselves into document files, such as Microsoft Word or Microsoft Excel. They possess the capability to send macro commands for automated tasks within the document files.
4. Trojan Horse
A trojan is a set of programs written to deceive users into downloading and installing them, believing that they can function as advertised by the programmer. However, after installation, they proceed to destroy or compromise data within the computer system, causing damage and distress to users who voluntarily downloaded them. It’s analogous to the story of the Trojan Horse, where the inhabitants of Troy brought the wooden horse inside the city walls, assuming it was a discarded item, only to find that hidden soldiers emerged from within the wooden horse to conquer the city from within. This is the origin of the term ‘trojan,’ which represents this type of computer malware.
5. Stealth Virus
This type of computer virus possesses the ability to stealthily disguise itself, often using a legitimate-sounding name. For instance, when a file contains an embedded virus, the actual file size cannot be accurately detected, as the virus has assumed control over the DOS. This makes the file appear normal, just like the original, although the file size cannot be properly viewed. In reality, the file has been tampered with by the virus, which operates covertly and awaits user interaction by prompting them to click on it.
6. Polymorphic Virus
This type of computer virus is exceptionally challenging to control and eliminate due to its self-copying capability, enabling it to spread rapidly and extensively in numerous formats. Presently, there is a considerable number of computer viruses with this nature, rendering a single scanning method insufficient to detect every instance of this type of virus. Therefore, antivirus software with higher and more comprehensive capabilities is essential to effectively combat these viruses.
7. File Virus
This type of virus is most commonly encountered in daily life, particularly among those who frequently download free software from the internet. These viruses embed themselves in the form of installation files, often with the .exe extension. Therefore, it’s crucial to verify the source and credibility of the website before downloading such program files. Neglecting this caution could result in inadvertently introducing viruses into one’s own computer.

Businesses, Take Note!
Preventing Computer Virus Infections in Your Company Devices.
Preventing and Resolving Computer Virus Infections in the Company’s Computers is crucial, as it can lead to customer dissatisfaction, revenue impact, and workflow delays. Direct computer system management is necessary, which can involve hiring dedicated staff or considering IT outsourcing for quality and cost-effectiveness. This includes overseeing software updates, virus protection, and efficiently addressing virus-related issues over the long term.

Virus Scanner
Computer viruses can spread across platforms and borders, infecting any connected computer worldwide. Therefore, antivirus programs are crucial. These programs, either through scanning or using scanners, detect and store unique virus signatures in a database. When a virus operates, the scanner follows these footprints in memory and boot sectors.
Antivirus software comes in various types, all with the common goal of identifying, blocking, and eliminating viruses. They use two main techniques:
1.File Examination: Suspicious files are compared against a Virus Dictionary to check for any virus-related information.
2.Behavioral Scanning: Programs, files, or storage devices like flash drives are examined for unusual behavior indicating a virus’s presence, which is then quarantined and removed.
As threats evolve, a robust antivirus with consistent updates is vital to protect against the diverse range of viruses, including those mentioned earlier. By choosing an effective and versatile antivirus, you can safeguard your computer and data, ensuring privacy and security.
12 dangerous computer malware viruses businesses should watch out for.
1. Clop Ransomware
Ransomware is malware that encrypts your files until you pay a ransom to hackers. ‘Clop’ is one of the latest and most dangerous ransomware threats, evolving from the well-known CryptoMix. It targets Windows users. Before encryption, Clop ransomware blocks over 600 Windows processes and disables several Windows 10 apps, including Windows Defender, Microsoft Security Essentials, and your installed antivirus. Its targets have expanded to entire networks, not just individual devices. Even prestigious institutions like Massachusetts Institute of Technology have fallen victim to Clop ransomware, affecting almost all Windows devices within their network and demanding ransoms.
2. Fake Windows update (Hidden Ransomware)
Hackers send emails advising urgent installation of Windows operating system updates or using deceptive emails to trick readers into installing the latest Windows updates. However, these emails actually contain hidden ‘exe’ files of ransomware, specifically the ‘Cyborg’ strain. This ransomware, once in your system, encrypts all your files and programs, demanding a ransom to decrypt them. Basic antivirus software can’t detect or block these emails. To safeguard against these threats, you need antivirus programs with advanced internet security features that can shield you from such dangerous emails.
3.Zeus Gameover
Zeus Gameover is a part of the ‘Zeus’ family. Sometimes referred to as Zeus Trojan, its objective is to access the banking details of your account and steal all your money.
4. RaaS
‘RaaS’ or ‘Ransomware as a Service’ is growing within the underground hacker community. The underground RaaS industry is flourishing, hiring professional hackers. This growth illustrates that spreading ransomware to people is easier than ever. Even those with no prior experience in designing or coding malware may engage in this.
5.News Malware Attacks
Hackers exploiting the COVID-19 pandemic to target victims use fake emails posing as outbreak-related information. Readers receive notifications to click on links for further learning, but these links contain malware that copies files on your device and steals your personal information.
6. Fleeceware
Fleeceware, originally more prevalent among Android users, involves apps like horoscope readers, palmistry, photo editing, and video editing. Once installed, merely trying out these apps triggers charges, even if you don’t make a purchase or uninstall the app. While this was previously common among Android users, it has now also spread to iOS.
ุ7. IoT Device Attacks
The popularity of IoT (Internet of Things) devices has grown in the year 2021. Smart speakers and video doorbells, for example, are becoming more common. Hackers are now seeking to exploit the potential of these devices. They target IoT devices because many lack sufficient storage for adequate security measures. These devices often have easily accessible information like passwords and usernames, which hackers can use to access user accounts and steal valuable data like banking details. Hackers can also use internet-connected cameras and microphones to eavesdrop and communicate with people, including children, through smart baby monitoring devices. These devices can serve as vulnerabilities in a company’s network, meaning hackers can potentially gain access to the entire system through insecure IoT devices or spread to other devices.
8. Social Engineering
Human beings can be the weakest link in any security system. This is why cybercriminals are turning to psychological tactics and deception to attempt to access personal data. They often start by posing as specific individuals and contacting companies or service providers. They ask questions about the victim’s accounts and manipulate customer support teams into sharing sensitive information. They then exploit this information to gain access to accounts and personal data, including payment details. While not a type of malware, this trend is concerning as hackers don’t need to be knowledgeable about encryption or malware development. Attackers rely on manipulating human psychology and exploiting human error, taking advantage of people’s willingness to provide information.
9. Cryptojacking
Cryptojacking malware is designed to assist in ‘mining’ digital currencies like Bitcoin. Mining requires significant processing power to generate new crypto coins. This is why hackers attempt to install cryptojacking malware on computers and mobile devices to aid in the mining process.
10. Artificial Intelligence (AI) Attacks
When there are additional tools available for developers who want to write AI scripts and software, hackers can use this technology to conduct powerful cyber attacks. While cybersecurity companies in the cyber world are using artificial intelligence and algorithms to help fight against malware, these technologies can also be used to hack devices and networks on a wide scale.
11. DogeRAT
“DogeRAT” is a new malicious malware on the Android system. The modus operandi of DogeRAT involves advertising on fake websites or various fake apps to lure users into downloading. Once inadvertently installed, it gains access to private data, financial information, and takes control of the infected mobile device.
12. Ahui Ransomware
Ahui Ransomware is a form of malicious software that employs encryption techniques to restrict access to files on the targeted computer. Once Ahui infects a device, it often appends the ‘.ahui’ extension to the encrypted files’ names and deposits ransom notes containing instructions for paying the ransom fee. These ransom notes provide guidance on how to make the payment to cybercriminals in order to obtain the decryption key needed to unlock the Ahui Ransomware-encrypted files. Ahui Ransomware has been identified as a variant within the STOP/Djvu Ransomware family and may be distributed alongside other types of malware, such as RedLine or Vidar.
The Xcitium program prevents and addresses Ransomware attacks.
It’s a 100% Endpoint Anti-Malware solution.
Xcitium is a Cloud-based Cyber Security technology that ensures security for devices both within and outside the organization. It works anywhere, on any device, and can be accessed at any time. With ADVANCED ENDPOINT PROTECTION, it offers compelling Endpoint Security for businesses to safeguard data from Ransomware, providing a high level of 100% advanced Endpoint protection assurance. It doesn’t trust or execute unfamiliar processed files, preventing potential damage.

What can the Xcitium program do?
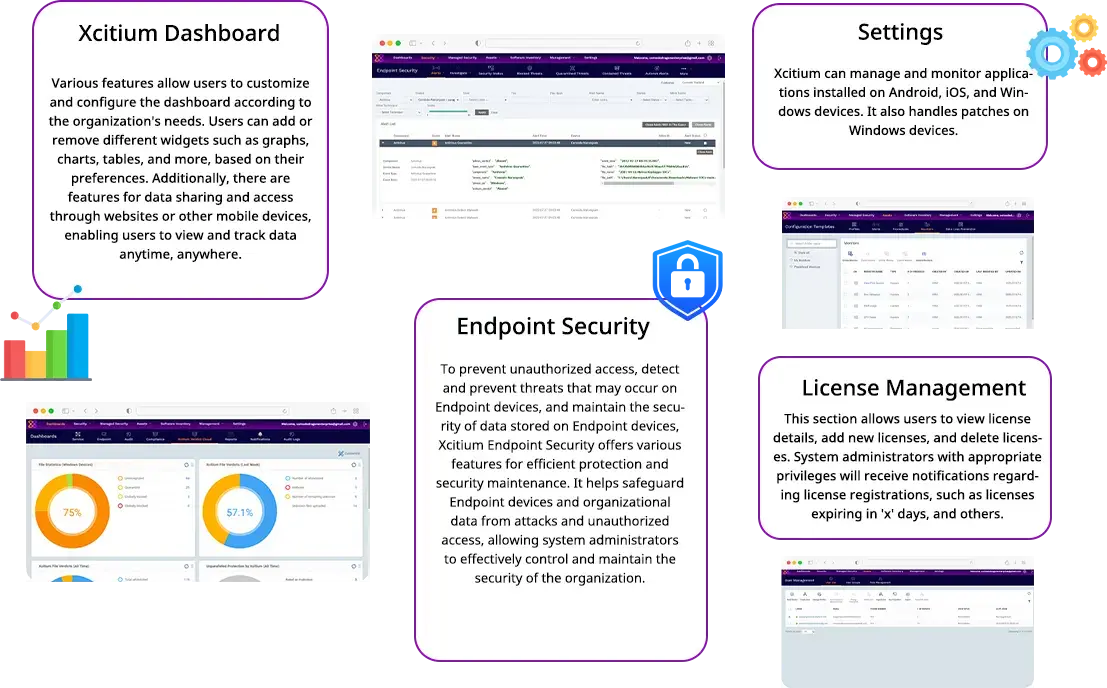
What are the advanced feature capabilities of Xcitium?
ZeroDwell Containment
Prevents unknowns instantly through denying write access privileges of any unknowns
NGAV & Award-winning Firewall
Powerful real world antivirus to automatically detect, cleanse and quarantine suspicious files
Fileless Malware Protection
Protection against fileless malware payloads that bypass any traditional antivirus
Virus Scope Behavior Analyzer
Protection against fileless malware payloads that bypass any traditional antivirus
Xcitium Host Firewall
Keep incoming threats out as well steer clear of any suspicious threats going outbound.
Host Intrusion Prevention System
Continuous monitoring of operating system activities to detect intrusions before any trespassing can occur
Verdict Cloud Intel Analyzers
Real time static and dynamic scans across the cloud, deep web, and dark web for unknowns against your organization.
Xcitium File Reputation Lookup
Cross reference any file’s threat reputation against one of the world’s largest whitelist and blacklist threat intelligence.
Cloud Based Updates
New malware signatures are consistently delivered through the cloud to ensure both security and optimal user performance.
How important is Endpoint Detection and Response (EDR)?
For those interested in installing the Xcitium program, you can easily use the AquaOrange service to facilitate the installation process for both business and personal devices. For more details, visit www.aquaorange.co.th/xcitium-thailand/





